Check The ISO 27001 ISMS blog for articles on information security management, ISO 27001 certification, NIST, cyber security, PCI DSS and more.
Designing an information management scheme
An information management scheme provides a framework within which information can be identified, its security requirements determined and instructions given to those who may handle it.
How to approach security measures and controls
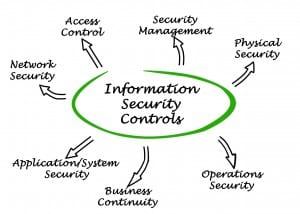
A control, or a security measure, is a tool for treating risk. Controls can reduce the impact or likelihood of a risk, thus decreasing its overall rating.
How to develop a Statement of Applicability in ISO 27001
The Statement of Applicability (SoA) is one of the key documents that you will need to produce for your ISO 27001 information security management system (ISMS).
Information Security Risk Assessment and Management
It is important to ensure that any corporate risk management strategy, risk management method and assessment methods are borne in mind when carrying out information security risk assessments.
What is the job of Chief Information Security Officer (CISO)
Since ISO 27001 does not require the CISO, it does not prescribe what this person should do. Generally, this person should coordinate all the activities related to securing the information in a company, and here are some ideas on what this person could do.
How to write your Information Security Policy according to ISO 27001
An information security policy is the cornerstone of an information security program. It should reflect the organization’s objectives for security and the agreed upon management strategy for securing information.