Let’s get you started.
Are you thinking about improving your information security posture?
Have you been advised to do it by a switched on customer to win or retain their business?
Perhaps you’re confused about jargon like ISMS or ISO 27001 and the options around it?
If you’re wondering how this all fits together or what you should do first, let’s start from the beginning…
What is an ISMS?
An Information Security Management System
describes and demonstrates
your organisation’s approach to Information Security.
It includes how people, policies, controls and systems identify, then address the opportunities and threats revolving around valuable information and related assets.
Cyber security is all about addressing technology led threats. Effective cyber security solutions are part of the broader ISMS.
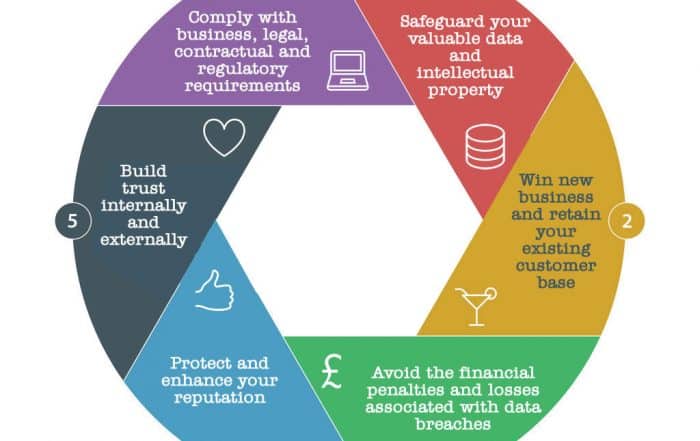
There are good reasons for you to invest in an ISMS
The facts speak for themselves…
The average cost of a security breach is £1.46m – £3.14m to a large organisation, and £75k – £311k to a small business.
Organisations face fines up to 4% of global turnover for a breach (under EU GDPR in 2018).
Suppliers will not get past basic customer evaluation criteria without effective information security credentials so there is little chance to grow a business.
Statistics taken from the Government Information Security Breaches Survey 2015 and a range of other recent reports on the subject.
Done well, an ISMS will help your organisation improve and grow.
What’s included in an ISMS?
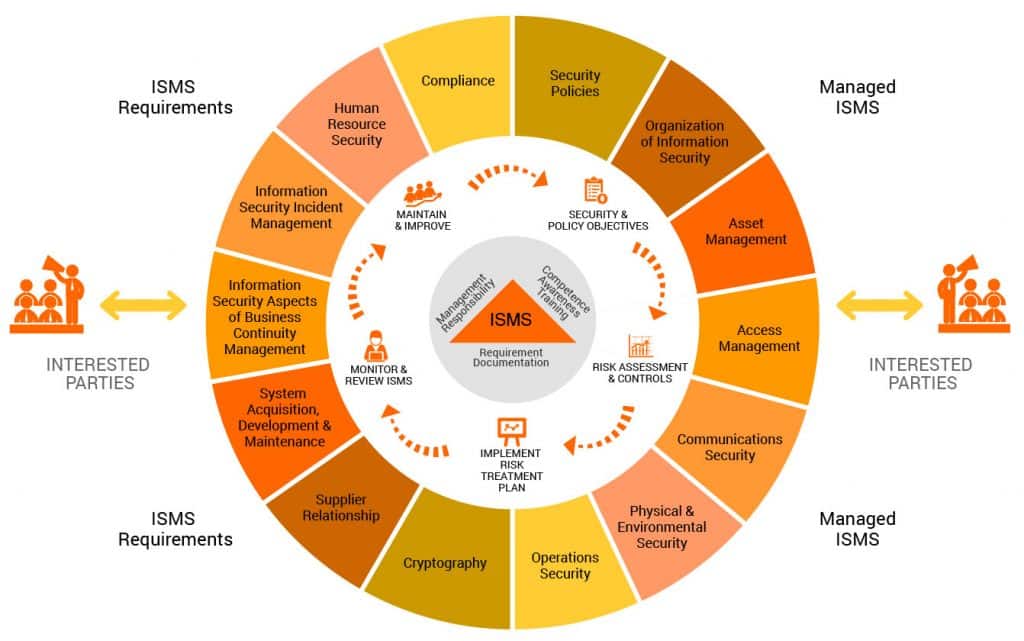
An effective Information Security Management System is made up of 5 elements, as shown in our pie chart.
The real size of these pie slices, in terms of time and cost, is all dependent on your objectives, your starting point, the scope you want to include in your ISMS, and your organisation’s preferred way of working.
Investing well in one slice will help reduce or avoid much larger investments in the other slices. But beware the pitfalls, such as following the cheap policy documentation route, as it will cost you much more in the long run.
A trusted ISMS will follow recognised standards
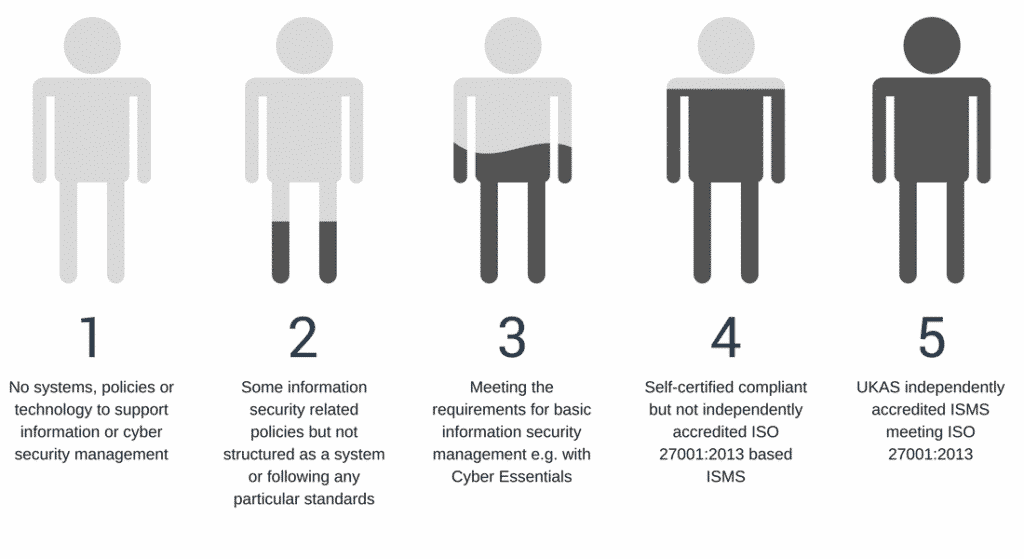
There are different levels of information and cyber security maturity, as well as different standards you can achieve to evidence compliance.
Those standards might be dictated by the nature of your business, its goals or your customer’s expectations.
Whatever your requirements, there is a proven approach that you can follow.
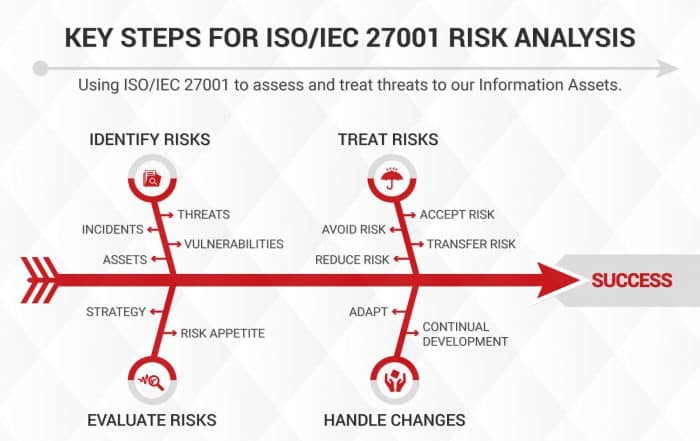
How to implement an ISMS ?
Now that you have a better understanding of ISMS and have considered what you should do, you’ll also be thinking about how to do it as well. Whether you take a DIY approach, or bring in others to help, those five pieces of the pie will need investment for ISMS success.
Why consider our powerful ISMS cloud software?
Your focus will be on growing your business, not spending time developing the tools and technology to manage an ISMS. After all, the opportunity cost of losing focus and time could be expensive.
There were no attractive solutions when we started out on the road to managing information security, and that’s why we built ISO27001.solutions. Now you can benefit too. We’ll equip you for success at a fraction of the cost and time of alternatives or you trying to build it yourself.
We make it simple
It’s easy to build your ISMS using our software solution. ISO27001.solutions facilitates improved results with everything you need for success in one secure online environment.
ISO27001.solutions capabilities include:
Take a walk in your customers’ shoes
Which supplier’s approach to information security would you choose to protect your valuable information?
Whilst achieving level 5, a UKAS accredited ISO 27001 certification, costs slightly more initially, the return from that investment is going to be much higher. You’ll be better protected from threats that might destroy your business, and prospective customers are much more likely to embrace your services. Your investment will be a fraction of the cost from winning and retaining business, or paying out from the costly data breach.