ISO 27001 – Information Security Management Standard (ISMS) – is all about safeguarding yours and your customers’ information.
This article will teach you:
- WHAT ISO 27001 is, how it works and the benefits certification brings organisations
- WHY ISO 27001 is so popular
- HOW organisations can become ISO 27001 certified
- WHO the most suitable Certification Body is to work with
- WHAT costs you can expect when becoming ISO 27001 certified
While ISO 27001 is one of the lesser known standards, compared to ISO 9001 and ISO 14001, it’s increasing in popularity and demand.
Until now, it’s been the 4th most popular standard after ISO 9001 for Quality Management, ISO 14001 for Environmental Management and OHSAS 18001 for Health and Safety.
However, that situation is changing. All businesses, charities, organisations and public sector bodies need to know what ISO 27001’s all about, what the implications are and what can be done to achieve certification to the standard.
The Federation of Small Businesses (FSB) are certainly taking this seriously. 42% of their members have been directly affected and The FSB are calling for all businesses to take steps and assess the risks of online crime and fraud. The FSB has published its CyberCrime strategy online.
This article will take you through the subject; the risks, the numbers and reasons why information security is so important. We’ll cover the problems and challenges you may face when implementing ISO 27001, the consequences of ignoring them and what you can do to prevent the problems arising in the first place.
HOW WE GOT HERE
For years, organisations have been primarily focused on making sure that physical security’s in place – that’s exactly what the insurance industry has demanded! If you failed to install the right padlock or levels of security, you could find yourself un-insured; which has made us all the more aware of physical security. The problem is that we’ve forgotten about information security.
We all have processes in place for locking up at the end of the trading day, including key holders’ responsibilities, tracking sets of keys and permitted access to premises. Nowadays, virtually all sporting venues have key coded doors to access changing rooms to reduce theft, and of course the same precautions are found in baby units at hospitals, nursery schools, etc.
We’re very good at protecting physical things; chairs, tables, plant and stock, but when it comes to information we’re not quite as diligent.
Businesses have been encouraged to identify risks of all shapes and sizes for years now, and once identified they must be managed, and risk mitigation must be considered. In the good old days, it was the physical risks that were so important, with a primary objective being to stay one step ahead of the thief!
First we had clear desks policies – putting away papers holding customer information. Filing cabinets were locked and confidential paper waste was shredded.
As soon as computers hit our desks, we had to start thinking about firewalls, anti-virus and malware, passwords, logins and access levels. As the internet and computer networks arrived, risks not only multiplied, but they became even more complex.
Having a password isn’t enough now these days. It must be ‘strong’ (letters, numbers and symbols included), regularly changed and usually combined with a PIN too, not to mention auto lock-outs now happen in minutes, rather than not at all. Clear screen policies have now been added to the clear desk policy too.
Privileged access levels are commonplace and that goes for key stroke monitoring too. Personal email protocols, spam filters, email list security and file attachment rules now pervade businesses and employee handbooks. Dropbox (and similar), once the storage device of choice alongside remote plug in drivers, has now been joined by a plethora of cloud storage systems. Plug in devices also raise security issues now too.
Backups for systems, data lists and intellectual property were usually done with a remote device that someone took home. Now, with rapid technology developments, backups are far more sophisticated and complicated. This in turn increases risks and makes them even more complex.
Keeping your website safe and compliant is a business priority, especially if it’s your main trading platform. Developing software is a challenge and upgrading existing software can be a problem too. Preventing your employees from uploading unchecked software is testing, but it’s best practice to put this in place. Encryption and SSL padlocks are now the norm on websites and e-commerce platforms, but all of this needs managing and protecting. Utilising open-source coding is standard for many organisations today, but do you really understand what you’re getting into?
Traditional pen and paper businesses are now conducted almost entirely on connected computers and stored in remote clouds that have portal logins for customers to access their files. Collaborative working, co-working spaces, home offices and coffee shop working continues to raise information security concerns and challenges.
Another big question: is wireless secure or not, and does anyone really care anymore? Surely all we want now is to be connected! Gone are the days of VPN, ISDNs installations; and now BYOD (Bring Your Own Device) is requested for seminars, workshops and training courses. We just plug in, log on and go – assuming that everything will be okay.
It’s certainly been a fast ride from the 1980s to today’s online, connected and casual world. But as the world has changed, so have the risks you need to be aware of, manage and mitigate.
What all organisations need is an information security minded approach, with processes that allow the right people to access the right data at the right time. Collecting, storing, accessing and using data securely and effectively must be the goal for every organisation. It certainly is a major priority for big brands, and should also be for you.
3 CAUSES OF DATA BREACHES
There are hundreds of security breaches that happen every day but in the end, they fall into 3 main groups:
- Malicious, intentional or criminal
- System glitches
- Human error
IBM 2015 Cost of Security Breach Survey conducted by Ponemon Research, allocates 49% to malicious activity, 23% to system glitches and the remaining 28% to human error.
- MALICIOUS, INTENTIONAL OR CRIMINAL
Just like the old fashioned theft of physical goods, these attacks are usually well planned, targeted and for the most part, have a negative impact on the business being targeted.
Many of us have had our email hacked or our phone tampered with by mischievous friends sending inappropriate texts to our contact lists. It can happen to anyone, it’s usually just a matter of time.
Phishing, scams, hacking, fraud, cybercrime, theft of intellectual property (company T&Cs are the most commonly stolen text), data, systems and diversion of funds. Viruses and system infections are also common. As businesses work hard preventing data theft by implementing more sophisticated systems, the perpetrators are working just as hard to always stay one step ahead.
E-commerce trading operations regularly undergo penetration testing and STAR simulated targeted attack response testing. This makes sure that their sites are safe and can continue to trade securely.
Just because you’re a small business doesn’t mean you aren’t a target. It might not even happen online – invoice fraud is an increasingly real threat.
- SYSTEM GLITCHES
Why is it that your network and computer were fine when you turned them off last night, but first thing this morning they don’t work? These problems happen; they are illogical and we never usually know the reason why.
Most of the time the problem is solved and everyone gets back to work with a sigh of relief. Investigations should be commonplace, but sadly they only happen in a few cases.
Where they do happen, it’s this diligent approach to understanding what happened and why that makes an organisations’ systems much stronger.
When a product is badly made, how do you know if the ingredients for your production recipe is a ‘system glitch’ or intentional tampering by a disgruntled employee? The only way to find out and stop it happening again is to investigate, find, resolve and monitor.
- HUMAN ERROR
The wonderful thing about people is that they are predictably, unpredictable! But as a manager this is a difficult one to manage because of the unpredictable nature of the risk, as you’re unlikely to get any warning signs.
The news is littered with stories of companies where employees have left laptops or paper files on trains, lost phones, shared passwords they shouldn’t have done, posted the wrong information at the wrong time on websites; the list goes on and on.
In the USA there’s a website dedicated to daily security breaches. It’s a great place to see the full extent of information security risks and is a bookmarked site for many IT specialists.
WHAT ARE THE CONSEQUENCES?
Let’s look at legal breaches first. Data Protection Act 1998 can result in prosecution, fines up to £500,000, loss of customer confidence and associated income levels. For many businesses this could lead to insolvency. In May 2018, the EU General Data Protection Regulation (GDPR) comes into force. From that date, breached organisations will find the fines they face increasing dramatically; with the new upper limit totaling €20 million.
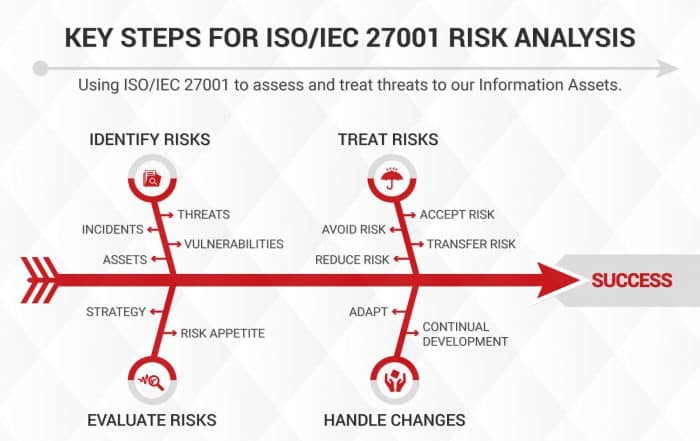
The international standard for Information Security Management, ISO 27001, summarises the information security elements of the majority of global privacy regulations – including Principle 7 of the Data Protection Act – by providing a comprehensive framework for developing, implementing and maintaining an independently auditable Information Security Management System (ISMS).
ISO 27001 helps organisations protect their data assets and meet their compliance objectives. An ISO 27001 compliant ISMS is a risk-based approach to Information Security Management that addresses the specific security threats an organisation faces, covering people, processes and technology.
Accredited certification to ISO 27001 is recognized across the world as the hallmark of best practice Information Security Management, and demonstrates to customers, stakeholders and staff alike that an organisation takes its data security responsibilities incredibly seriously.
ISO 27001 is the best practice framework for an Information Security Management System
OTHER CONSEQUENCES
According to UK Government, 72% of small businesses experienced a security breach in 2015
COMPLACENCY CAN BE FATAL
All too often we say; ‘it won’t happen to me’ – but it can, and does. Burying your head in the sand isn’t good enough anymore, there’s far too much at stake.
How would you feel if it was your personal details left on a laptop on a train, or your banking details hacked from a supplier? How would you feel if you were a sweet manufacturer and someone tampered with your secret recipe which meant children became ill? Just another example of a security breach.
What if one of the invoices you paid had been tampered with, meaning you paid a criminal instead of your client and you’d have to pay it again? What checks and balances do you have in place to make sure your money is in the right account?
You certainly don’t want it to happen to you, but how can you answer your customer’s question; “Can you prove that my data is secure?” Rest assured it won’t be long – just a few more public breaches – until more and more people start demanding proof of secure data information from their suppliers.
It’s so important for everyone; shareholders, customers and employees, that you have this under control. ISO 27001 is a good place to start
IT’S NOT JUST THE IT DEPARTMENT
Information security isn’t just about websites, clouds, emails and apps. It’s about everything in your business or organisation; secret recipes, trademarks, patents, copyright, data, processes and company assets.
ISMS applies to everyone, wherever they are and whatever they do in your organisation.
You’ll need to consider systems and procedures that everyone must follow. This will help you to reduce the risk of someone forgetting, or doing something wrong – which leads to a breach.
Don’t restrict your policies to only your direct employees. You need to think about others who have access; your outsourced bookkeeper, contractors, interims, freelancers and interns. Anyone who has access to anything in your business should be included.
Often overlooked areas are your web and marketing agencies, payroll providers and accountants. The agencies usually take a feed of your customer data into their systems to enable them to send email marketing campaigns on your behalf. How do you know if they are keeping your data secure, and what checks do they have in place to make sure they use the right list with the right communication?
Your money advisers may be emailing your sensitive company data or might not be holding it in a secure location – either on or offline.
Do you email your accounts to your accountant and vice versa? What happens if it arrives at the wrong destination? Anyone that you share information with, ought to be able to prove to you that it’s secure.
Shouldn’t you insist that your suppliers have ISO 27001 certification as well?
We always want to believe the best in everyone. But there are many bankrupt companies because one partner didn’t play by the rules whilst the other partner didn’t have any checks and balances in place to highlight that something wasn’t right.
Nick Leeson, – ‘the infamous trader whose unchecked risk-taking caused the collapse of Barings Bank’ – proved that uncontrolled employees or partners can be extremely dangerous to a business and its customers. Unsuspecting customers are usually the victims, leading to emotive and high profile reporting, which in turn causes significant brand damage and lost income.
As a business manager, leader or owner, you have a duty of care to manage information security and mitigate the risks.
…That’s where ISO 27001 can help!
Now a question for you…
When was the last time you reviewed your online privacy policy, do you know what it says, the implications it puts on you and how you are performing against it?
You should!
HR AND INFO SECURITY
Because of the human element, HR has a big role to play in an organisations’ Information Security Management. From hiring the right people, to setting the policies and policing them – HR is at the heart of this.
2 true stories from the Serious Crime Directorate of Kent Police:
- OPERATION QUEST
Essex based company had a disagreement with their senior IT employee. This resulted in the company dismissing the employee and as a parting shot telling him he would not be paid anything further by them.
The company however, didn’t take swift action in removing the now ex-employee from their network. As such, within a day he’d gained remote access to their system and destroyed key files required to operate their business and corrupted the backup files.
Although the suspect was arrested and is currently on bail, this doesn’t retrieve those files back for the company and they’e only now, some 3 months later, starting to operate more smoothly. - OPERATION JEROME
An IT employee from a Kent based company left and joined a rival company taking the username and password for the IT system. This was provided to 5 company directors of his new company. Over a large period of time they’ve used the provided credentials to intrude onto the victim’s server and obtain confidential business information, allowing them to takeover customer contracts by undercutting pricing. Currently in the court process.
These stories illustrate perfectly why HR, alongside line managers and people management, must be closely involved with the ISMS. Here are some of the areas where HR can contribute:
- Confidentiality clauses
- Non-disclosure agreements
- Data protection – helping to define sensitive employee information
- Employee handbook with relevant policies
- IT usage
- Email usage
- Internet usage
- Downloading programs
- 3rd party software
- Clear desk and clear screen policies
- Bribery, ethics and business protocols
- Termination of employment
- Passwords
- Recruitment policies
- Employee health and personal details.
STEP 1, STEP 2, PROOF…
Your physical security’s most likely in place; with doors locked and alarms set when you’re not there. Your firewall, spam filters and antivirus are also most likely up and running 24/7. You’ll also have some written processes, procedures, ways of doing things, checklists and monitoring in place.
All that means you’re well on your way to having an Information Security Management System in place. Having an ISMS in place means you’ve already completed step 1 in proving to everyone that your data is secure. Gaining certification to ISO 27001 gives you step 2; and ultimately the proof.
ISO 27001 proves you take Information Security Management seriously.
Now you can prove to your customers, both existing and potential, that you not only take information security seriously, but that everyone in your organisation is information security aware, and that you have systems, processes, procedures and monitoring in place to make sure everything is right.
An effective ISMS means everyone and everything in the organisation is involved.
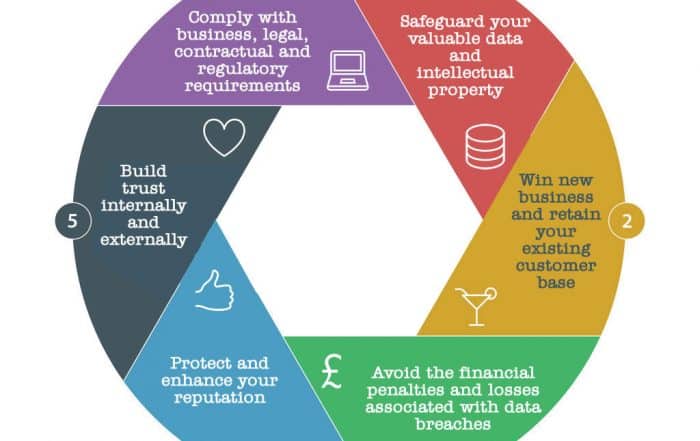
BENEFITS OF ISO 27001
Now you have content customers, you’ll also start to experience a number of other benefits:
ISO 27001 delivers more than proof… It saves money too
WHAT YOU NEED TO CONSIDER
As with anything new in an organisation, it has to be driven from the top; so great leadership is needed. You’ll need an ‘ISO champion’ with a public mandate to implement the ISMS, as directed by the senior management team.
You’ll need to comply with Data Protection Act 1998 and any codes of practice and/or regulations for your industry. These are varied, but most will also help towards your ISMS and gaining ISO 27001.
You’ll need to understand exactly what needs to be protected and why. Then you’ll work on the how – data, IP, processes, personal details of employees and customers, payments, trade secrets, etc.
A commitment to ongoing improvement is needed. You can’t take your eye off the ball once you have your certificate – you have to maintain it. There’ll be an annual audit to make sure you’re still up to scratch – if not you’ll risk losing your certification.
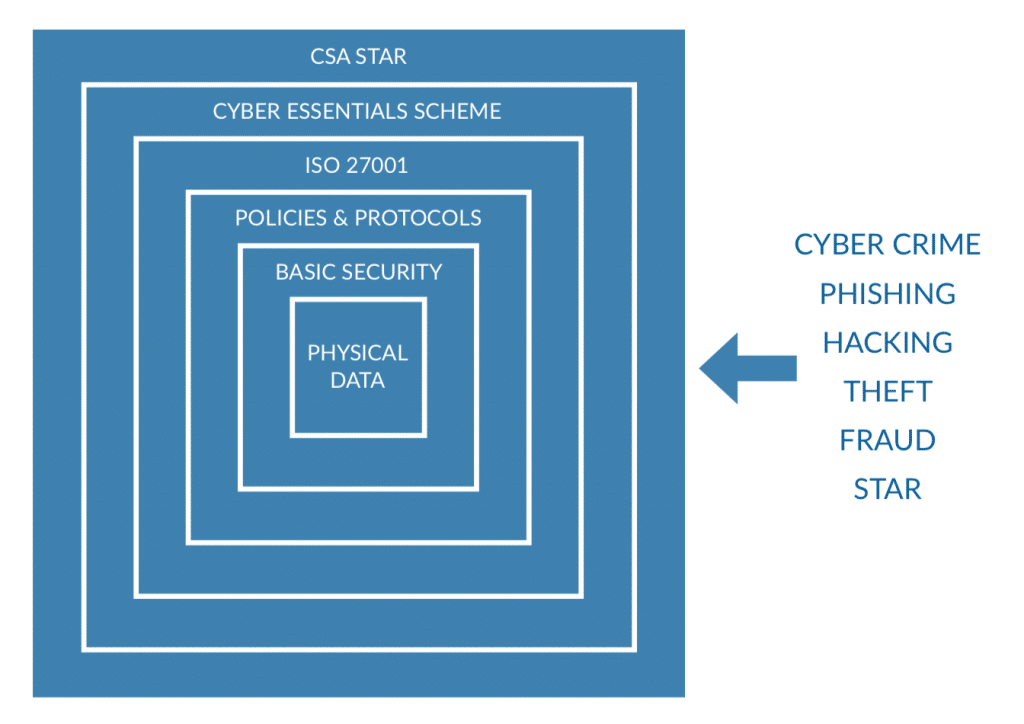
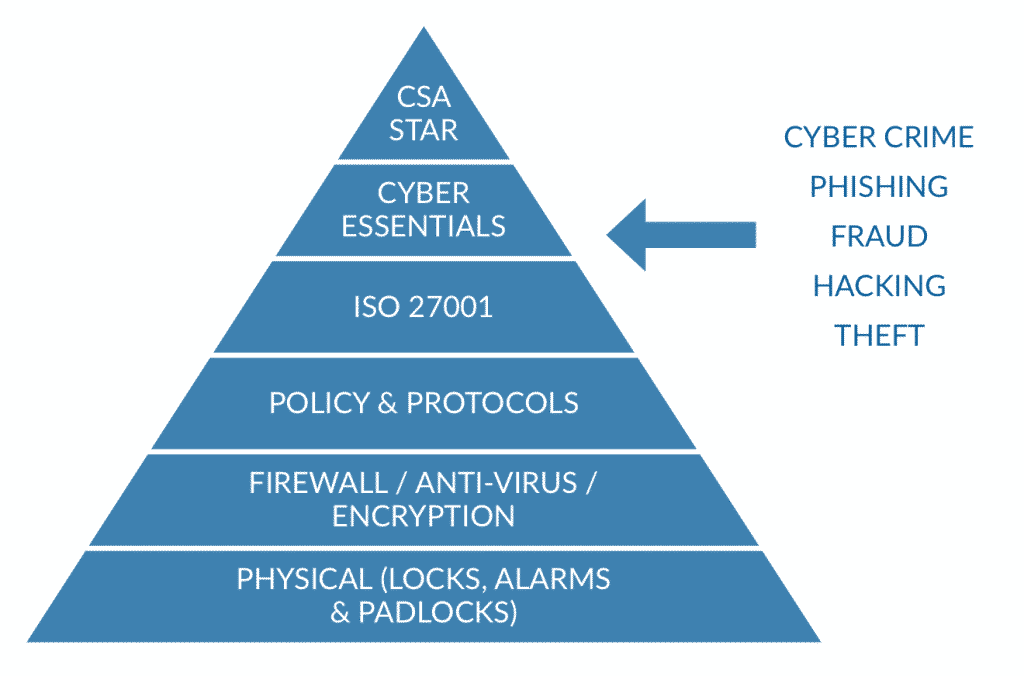
As this diagram shows, ISO 27001 is a step towards a better Information Security Management System, but there are many other cyber risks that could hit your organisation which don’t necessarily fall under ‘information’.
- CYBER ESSENTIALS
This is a government-backed, industry supported scheme to help organisations protect themselves against common cyber-attacks. It’s a set of basic technical controls for organisations to use. Backed by the FSB, The CBI and a number of insurance organisations; it enables organisations to gain 1 of 2 new Cyber Essentials badges.
Interestingly, the government requires all suppliers bidding for certain sensitive and personal information handling contracts to be certified against the Cyber Essentials scheme. - CSA STAR
CSA STAR (Security, Trust and Assurance Registry) refers directly to cloud computing. While not currently demanded by government or other organisations, it’s been developed to answer the concerns of the Cloud Security Alliance (CSA). The CSA also developed the Cloud Control Matrix (CCM).
CSA STAR will help businesses adopt cloud services – as cloud service providers, in particular, can give customers proof that the data they hold is secure. - CYBER INSURANCE
The Association of British Insurers defines cyber insurance as ‘covering the losses relating to damage to, or loss of information from IT systems and networks’.
Their website has a wealth of information about what is and isn’t covered, as well as information for you to decide whether or not you need the insurance protection.
CERTIFICATION PROCESS
1. PRE-ASSESSMENT
Outside of the various training courses and seminars help by Certification Bodies, many offer a ‘Pre Assessment’ or ‘Gap Analysis’ service ahead of the formal certification process to identify any omissions or weaknesses. Alternatively, some choose at this point to use a consultant to give added confidence. Again, many Certification Bodies have an answer to this, in the form of a consultant register. While they’re not permitted to recommend consultants, they can provide details of specialists who are known to them.
2. STAGE 1 AUDIT
The 1st assessment, referred to as a ‘Stage 1’ Audit is a document review, with the aim being to establish that – on paper at least – you’re conforming to all the requirements of ISO 27001.
The length of the Audit is determined by factors such as your organisations size and the industry you’re in. This will influence the cost, so you’ll be informed of the amount of time required in the form of an Audit Plan in advance.
Once the Stage 1 Audit is finished, there’ll be a closing meeting to round-up the findings. You’ll be provided with a report detailing what happened during the Audit, with an overview of any non- conformities.
3. STAGE 2 AUDIT
In order to be recommended to move forward to the ‘Stage 2’ Audit, you’ll need to close out any non-conformities by establishing a Corrective Action Plan. Much like a driving test, non- conformities are separated by minor and major variants. Whereas major variants need to be acted on immediately, minor non-conformities can be reviewed at the next Audit.
The Audit itself is about demonstrating that your organisation’s living and breathing what you’ve documented. Your Auditor will therefore need to meet with managers and staff, as well as see evidence of your Internal Audits and management reviews, as documented in the requirements of the standard.
All being well, you’ll be recommended by the Auditor for certification. However, this’ll require final sign off by the Certification Body’s compliance department. You’ll then receive a report and any non-conformities will need to be acted on before certification can be formally awarded.
4. ANNUAL AUDIT
During Audits, Auditors are encouraged to share Opportunities for Improvements (OFIs) in the spirit of establishing an ethos of continuous improvement.
These are reviewed at Surveillance Audits, which must occur at least annually. In the meantime, you should maintain a schedule of Internal Audits and management reviews.
Most Certification Bodies issue certificates in- line with the 3 year certification cycle. Every 3rd year, a ‘Re-Certification’ audit is carried out. Whereas a Surveillance Audit will focus on improvement areas found in previous audits, the Re-Certification Audit must cover all of the standard’s requirements.
As a result, it can take longer than the more frequent Surveillance Audit, and cost more as a result.
There were more than 148,000 victims of fraud in the UK in 2015 – The average total cost of a data breach in 2015 increased to £2.53 a 56% increase since 2014 million, from £2.37 million in 2014.
USING A CONSULTANT
The alternative for seeking out internal representation is to look for a specialist ISO consultant in ISO 27001. There’s an extensive network working in the field of the Information Security Management Standards (ISMS).
A consultant’s often used for very different reasons, depending on the size of the organisation. While a small business may require the hands-on help from being resource limited; a larger organisation may have the required manpower, but feel expertise is required to maximise efficiency opportunities and ensure the organisation meets more complex legal requirements.
Being in a position of reliance has its dangers – while a consultant may help overcome short- term challenges, there’s a risk that long-term dependency could negate the cost-benefit from implementing ISO 27001.
It could become attractive to simply leave all things related to information security management to the consultant. The downside though, is that while this may ensure your organisation continues to meet the requirements of the standard, you’ll fail to reap the rewards due to a lack of team participation.
Your decision will ultimately be based on your motivation to implement ISO 27001. The potential issue described may not be considered a problem if certification will lead to lucrative work in the long run.
However, ensuring your consultant works to engage, involve, train and empower your staff means you’ll avoid ISO 27001 simply becoming a cost to the business if the valuable contracts dryup.
When seeking a consultant, sector-specific experience is likely to be the most key factor for choosing the most appropriate person for the job. In combination with an impressive CV and collection of testimonials, it’s a notable advantage for the consultant to have auditing experience.
With some requirements of ISO 27001 coming down to interpretation, having a qualified consultant acting on your behalf means you can have confidence if challenged by the Auditor of your Certification Body.
CHOOSING A CB
The financial industry has the FCA, holiday companies have ABTA, but there’s no such mandated regulatory body for Certification Bodies. As a result, there’s no protection for those who mistakenly choose the wrong path. It’s critically important to make the right choice before signing on the dotted line.
Driven by government contracts requiring certification, the UK represents a significant proportion of worldwide ISO 27001 certificates. This demand has created an environment for opportunists to take advantage of those organisation who require certification urgently in order to qualify for a contract.
While the majority of Certification Bodies seek to demonstrate their competence and credibility through accreditation from UKAS, the UK’s National Accreditation Body, others have sought “accreditation” from alternative bodies. Whereas UKAS is recognised and supported by Government, the alternatives are recognised only by themselves.
The long-term issue with this is that, once spotted, non-UKAS certificates are often rejected and – just as importantly – the credibility of ISO standards as a whole is diminished by those not implementing them in the intended spirit.
UKAS’ role is to ensure Certification Bodies meet the ISO 17021 standard for conformity assessment. Achieving accreditation from UKAS involves a rigorous head office review of management, policies and procedures. Certification Bodies must also pass a test of their competence via Witnessed Assessments undertaken by UKAS.
Often, Certification Bodies without UKAS accreditation claim to be a ‘one stop shop’ for consultancy and certification, in an effort to market themselves as the most convenient option. However, this is in direct violation of ISO 17021’s requirements – Certification Bodies must remain impartial and can only provide certification, and not consultancy.
CERTIFICATION OR ACCREDITATION?
For most, certification and accreditation are interchangeable terms.
However, in the world of ISO standards, there is a hierarchy – Certification Bodies are accredited by National Accreditation Bodies.
As a result, an organisation can only be ISO 27001 certified, not ‘accredited’.
THE COST OF ISO 27001
Costs of implementation have been left until last, as the chosen approach will have a significant impact. It’s a realistic ambition for an SME to implement and achieve certification to ISO 27001 without external assistance, and costs will be reduced as a result.
It’s important to assess the impact of the resources required and it’s important a cost-benefit assessment is carried out against other potential initiatives and investments the organisation could be making.
All Certification Bodies follow a similar approach, as cost is ultimately influenced by the time required to Audit, the amount which is derived from an industry-agreed calculator that takes into account:
- Staff numbers
- Industry
- Complexity and risk
- Number of sites.
A small company in the service industry may require just a couple of days of Auditing for the whole certification process, thanks to the relative simplicity of its processes. On the other hand, days required to Audit a large multi-site manufacturing site could move into weeks.
As long as a site duplicates activities of another, it can be ‘sampled’. Rather than Audit every site at great cost, visits can be rotated within the 3 year certification cycle.
The organisation’s industry sector and complexity means only certain Auditors have the appropriate knowledge, experience and qualifications to Audit. This’ll have a knock-on effect for costs, with Certification Bodies typically charging between €700 (£600) – €1.000 (£900) per day.
Beware of hidden costs on top of the Auditing! Management and travel fees are often excluded from quotations. It’s also important to check the length of a contract, as a lower fee may indicate less flexibility in the form of a lengthy agreement; where 3 years is typical.
Increasingly, Certification Bodies will quote a package cost inclusive of the Stage 1 and Stage 2 Audits, as well as the compliance and administration aspects. Despite this trend, it’s still important to check for hidden costs.
These same principles can be applied loosely to the cost of using a consultant. With day rates ranging from €450 (£400) – €1.100 (£1000) a day, it’ll be important to balance the level of support required with the value it will deliver.
ONGOING COSTS
Maintaining certification to ISO 27001 is subject to an Annual Surveillance Audit.
Some Certification Bodies will expect to see an organisation at more regular intervals based on their size and complexity – but this isn’t mandated by the standard.
AND FINALLY…
We hope that you’ve found this article not only interesting, but informative too! We’re on a mission to make sure that businesses have great management systems in place so they can operate more effectively and efficiently, have happier customers who buy again and again, and new customers clamouring to buy too. In the end, if businesses make more money and organisations are able to reduce costs, then we’re proud to have helped.
We work with a wide and diverse range of clients, from sole traders to government departments. Each one of our clients has unique requirements and we relish each challenge. However, we never forget that it’s your baby and that you’ll always want the reassurance of a safe pair of hands.
We have over 25 years’ experience in The ISO 27001 certification industry, winning multiple awards along the way to help demonstrate our commitment to delivering the best service possible.